Thanks to everyone who came out today! We had one of our largest turnouts and a great meetup. I met several new people who I hope stick around.
For those interested in the notes from today, they are posted below.
We did have one crazy person who called the police because some people were standing in a park. As far as we can tell, TPD did drive by and observed that, yes, there were people standing in a park, and then the police cruiser kept on going. It was a very mild disruption with the crazy person shouting for a short period of time, and I don't plan to let that deter me from getting together with you all in the future.
However, next week we will be meeting in a different park. We've talked about rotating locations in the past and we think it will reduce the chances of that crazy person bothering anyone again. I will post that alternate location when I put up the meetup info.
Internet Communications and Security Best Practices
The big picture: Security, resiliency, and convenience.
• Security and convenience are often at odds.
• Resiliency through picking better comms channels, and having alternate options.
• “But I’m not doing anything wrong! I have nothing to hide!”
◦ Yes, you do have things to hide, from someone.
Who are you worried about getting at your data?
• Corporations who do not have your best interests at heart…
◦ Example: Discord releasing lists of users for chat groups it was hosting.
◦ Example: Facebook trying to manipulate you to vote the way that maximizes it’s profit.
• Malicious individuals or non-governmental groups.
◦ Solarwinds hack…
◦ Generic hackers for profit.
• Assume that the federal government has access to most of your data, and has informants present in every group you participate in. I am not presenting this information to help you mitigate that.
Recent Computer Security Concerns:
• Cloud computing, cloud storage…
• Software as a Service, AKA “You’ll own nothing, and you’ll be happy.”
◦ Massive reduction of resiliency.
• How much do you trust Microsoft, Google, and Apple?
• Recent security ‘improvements’: Taking security out of the hands of the user.
• The problems with app stores…
◦ The problem with updates.
◦ What if you want an app they don’t want you to have?
• Pros and cons of open source software such as Linux:
◦ More people watching who will catch a problem. Generally, more secure.
◦ Less chance of getting locked-in to a certain vendor, who can then use that as leverage over you.
◦ Generally lower cost.
◦ Some expertise required, depending on what you’re trying to do.
◦ Poor support from some vendors.
◦ Project quality varies wildly, depending on who’s working on it.
◦ Difficult monetization strategy reduces quality of result.
Email Concerns:
• Who is hosting the mail, and how do they make their money?
◦ Examples: Google, microsoft, yahoo vs comcast vs protonmail vs self-hosted server.
• What is encryption, and who does that protect from? Who doesn’t it protect from?
◦ Example: Protonmail
◦ OpenPGP
• Good operational security practices:
◦ Multiple email accounts, one for each purpose, ideally with separate logins.
◦ How easy it is to send email to the wrong person.
◦ Using TO vs BCC. Who is your email going to? Does each person receiving the email know the identities of everyone else who’s included?
Text Message / Chat Options:
• Same problems as before: Who hosts it, who has the user list, how is it encrypted?
◦ Note: Metadata doesn’t contain the message itself, but is still extremely relevant to opsec.
• New problems: Are temporary messages really temporary?
• Options / Examples:
◦ Signal
◦ Discord
◦ Mumble or XMPP
What are VPNs (Virtual Private Networks)?
• What a VPN does do:
◦ Prevents tracking of you via IP address from a third party, while the VPN is on.
• What a VPN does NOT do:
◦ Protect you from malware attacks on the device that you’re using.
◦ Make you truly ‘anonymous’ or ‘invisible’ to governments. Who hosts the VPN, and how do you know they aren’t logging all that data?
• If you ever log into a website while not connected through your VPN, they now have an IP they could potentially trace back to you.
• If you use a browser that allows storing cookies, those can be used to unmask you once you disconnect from the VPN.
• If the machine you are using is compromised in some way, your VPN will not protect your identity.
All About Smartphones:
• General phone issues:
◦ All mobile phones, including non-smart phones, are trackable to a general area based off of the cell tower connection data. If your phone is on, with data enabled, and with you, you can be tracked to a small area (larger in rural areas) without any apps or other spyware involved.
◦ If you turn off your phone or data, that is also recorded in the cell tower data.
◦ A phone without a SIM card can still dial 911, so for true emergencies you can have an inexpensive backup that isn’t being tracked.
• Having no smartphone is a significant reduction in capability.
• Apple phones:
◦ No real access to operating system parameters. I have no idea how you would even try to make these secure.
• Android phones:
◦ What is Android? Is Android really Linux?
◦ What security flaws exist the moment you get an Android phone?
◦ Google app integration: Pros and cons. What alternative apps exist?
◦ Can you really get rid of Google? Maybe.
◦ Threats from other apps you install, and how to minimize them.
▪ Fewer apps is better…
▪ Reducing permissions.
◦ What is root, and how would you get it on your device.
▪ Dangers of root…
▪ Problems with updates...
◦ What is a firewall, and how to configure it. Non-root firewalls are lies…
• Pure Linux Phones:
◦ New options coming out, great potential.
▪ Librem 5 and Pinephone.
▪ May be able to run Android apps on Librem 5 in the future, but those with advanced features (any ‘security’ features) are unlikely to ever work.
◦ What you would lose without an Android or Apple smartphone:
▪ Example: Airline mobile apps, and how to work around it mostly.
▪ Mobile banking apps: Unlikely to ever work, unless Linux phones become very popular, because banks prefer you to use a device that another corporation controls.
▪ Unusual devices are generally more expensive and less well supported since they are a niche market and do not benefit as much from economy of scale.
[I'm reposting this to the top because we have a number of people who still need to get their ham license!]
For anyone near Tucson who hasn't already gotten your Ham license or is interested in upgrading what you already have, here is some info based on my experience of getting my Technician and General licenses recently:
- Free testing is available monthly in Tucson. Next event is March 8th @ 7PM . https://k7rst.org/testing.html
-- There is no preregistering. You just show up, but I highly recommend being there a half hour early to get in line. I was there 15 minutes early and waited a little more than an hour before it was my turn to take the test, and then there's more waiting in between exams if you take more than one.
- There is also an online testing option available now. It generally costs ~$15 and you need fairly decent internet, a computer with a webcam, and a phone with a camera. (Thanks to @freebirdie for sending me the info on this).
-- Look here to find a session that's open: ...
I've been meaning to document this for quite awhile but things kept getting in the way. I've been writing this slowly over the past several weeks now, and am finally ready to post it!
I've created a simple automated planter for low-effort food gardening that seems to work pretty well for a a decent number of different plants. This was originally inspired by Larry Hall's "Rain Gutter Grow System", and then I fused it with the general concept of bottom-watered reservoir planters, which you can find everywhere.
Larry Hall's video should show up at the end of this post:
One implementation of a standard, non-automatic, bottom-watered reservoir planter:
https://www.amazon.com/GroBucket-Watering-sub-irrigated-Container-portable/dp/B079CT29RZ/
My goals were to keep costs relatively low, minimize water usage, and minimize the weekly time I need to put in to maintain the garden. I don't mind spending a bit more time to get something set up if that means I don't have to remember to do another ...
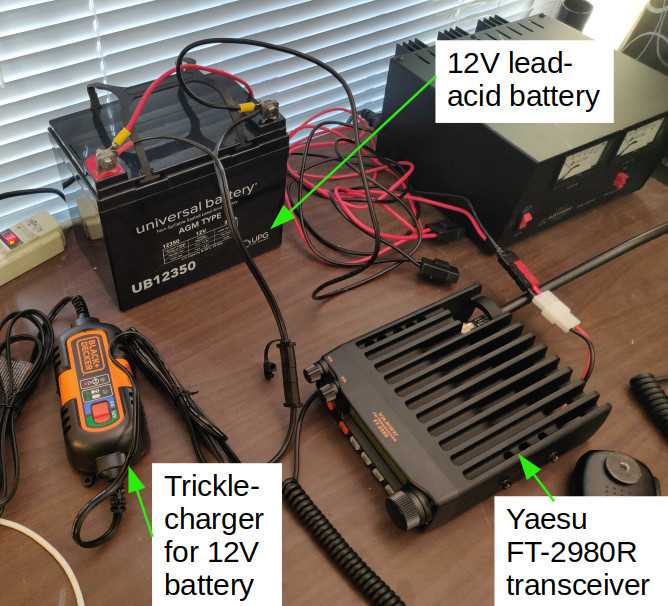
I've recently upgraded my VHF transceiver capability, and it has made a huge difference. We ask everyone to have a radio of some sort, and the cheapest Ham radio that works is the Baofeng UV-5R. I don't want to ask people to spend a ton of money, but from my own experience I do think upgrading is worth the extra expense. The receive electronics on the UV-5R are low-quality so they don't seem to work well with external antennas. A lot (or all) of the advantage you'd get from putting an external antenna up on your roof is lost when you plug it into the UV-5R.
The tranceiver I bought is the Yaesu FT-2980R:
https://www.hamradio.com/detail.cfm?pid=H0-015771
Unfortunately they just raised the price by $20, but it's still only $150 (or closer to $170 with shipping and tax). Note that it's a VHF only radio and is very simple compared to the more expensive models, but it is a beast of a machine that can dump 80W of power if needed.
This radio works well with every external antenna I've tried, and it's well suited to ...